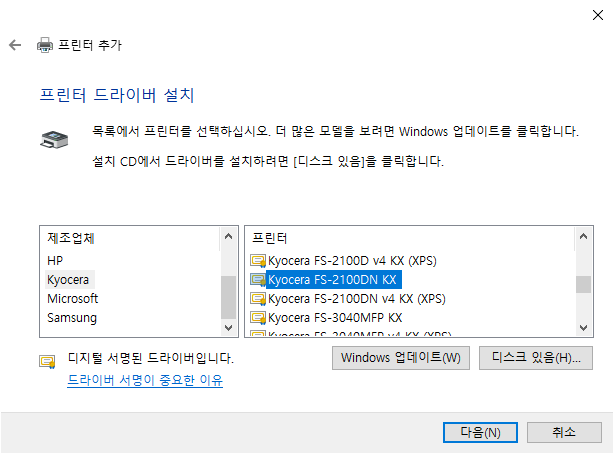
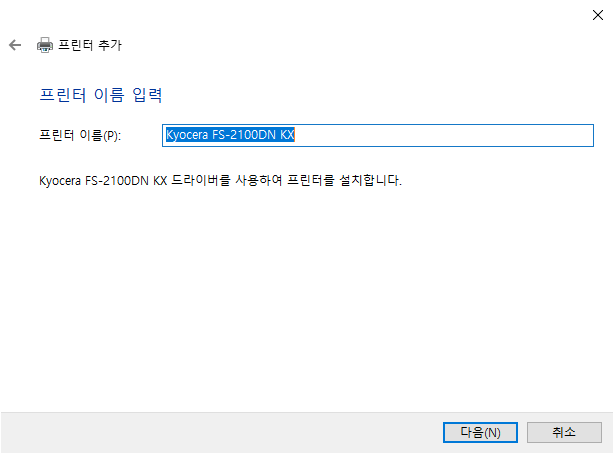
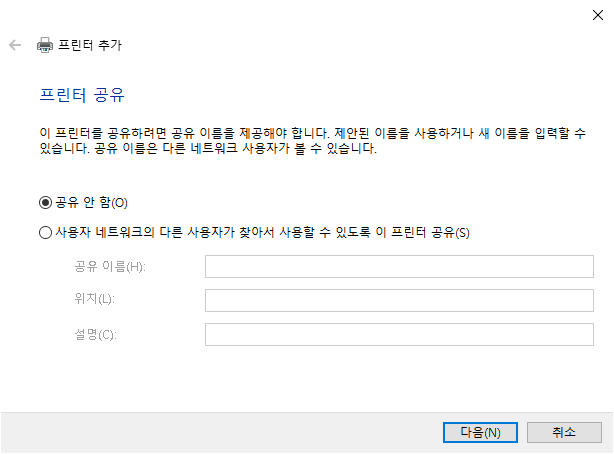
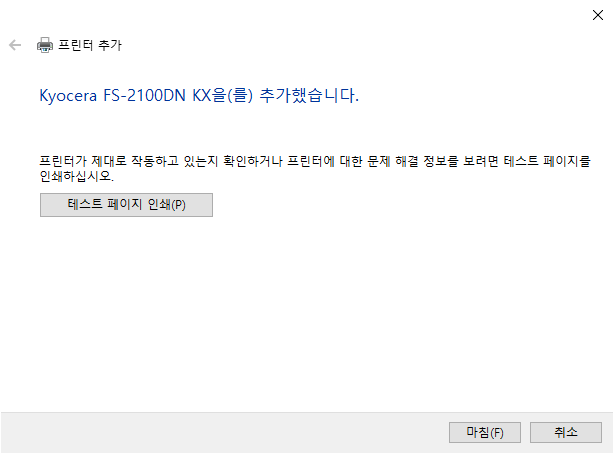
1. Download Windows PE add-on for the Windows ADK for Windows 11, version 22H2 and install.
In this example, Windows ADK Folder (default, C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Windows Preinstallation Environment) is %PEFOLDER% and the TFTP Server Root is %TFTPROOT%
2. Patch BCD in %PEFOLDER%\amd64\Media\EFI\Microsoft\Boot\
- Change the path of Boot Manager to our file, \bootx64.efi
> bcdedit /store BCD /set {bootmgr} path \bootx64.efi - Disable Integritycheck and Change Bootmenupolicy to Legacy
> bcdedit /store BCD /set {bootmgr} nointegritychecks Yes > bcdedit /store BCD /set {default} bootmenupolicy Legacy - Since linux file system treats file and directory names as case-sensitive, ramdisksdipath need to be modified in case that PXE is served on linux server
> bcdedit /store BCD /set {7619dcc8-fafe-11d9-b411-000476eba25f} ramdisksdipath \Boot\boot.sdi - Entries of patched BCD should be identical to:
> bcdedit /store BCD /enum all Windows Boot Manager -------------------- identifier {bootmgr} path \bootx64.efi description Windows Boot Manager locale en-US inherit {globalsettings} nointegritychecks Yes flightsigning Yes default {default} displayorder {default} toolsdisplayorder {memdiag} timeout 30 Windows Boot Loader ------------------- identifier {default} device ramdisk=[boot]\sources\boot.wim,{7619dcc8-fafe-11d9-b411-000476eba25f} path \windows\system32\boot\winload.efi description Windows Setup locale en-US inherit {bootloadersettings} isolatedcontext Yes osdevice ramdisk=[boot]\sources\boot.wim,{7619dcc8-fafe-11d9-b411-000476eba25f} systemroot \windows bootmenupolicy Legacy detecthal Yes winpe Yes ems No Windows Memory Tester --------------------- identifier {memdiag} device boot path \efi\microsoft\boot\memtest.efi description Windows Memory Diagnostic locale en-US inherit {globalsettings} EMS Settings ------------ identifier {emssettings} bootems No Debugger Settings ----------------- identifier {dbgsettings} debugtype Serial debugport 1 baudrate 115200 Global Settings --------------- identifier {globalsettings} inherit {dbgsettings} {emssettings} Boot Loader Settings -------------------- identifier {bootloadersettings} inherit {globalsettings} {hypervisorsettings} Hypervisor Settings ------------------- identifier {hypervisorsettings} description Hypervisor Settings hypervisordebugtype Serial hypervisordebugport 1 hypervisorbaudrate 115200 Device options -------------- identifier {7619dcc8-fafe-11d9-b411-000476eba25f} ramdisksdidevice boot ramdisksdipath \Boot\boot.sdi
3. Upload required files to TFTP server (For linux servers, capitalization DOES matter)
- %PEFOLDER%\amd64\Media\EFI\Boot\bootx64.efi to %TFTPROOT%\bootx64.efi
- %PEFOLDER%\amd64\Media\Boot\boot.sdi to %TFTPROOT%\Boot\boot.sdi
- %PEFOLDER%\amd64\en-us\winpe.wim to %TFTPROOT%\sources\boot.wim
Or customized windows 11 based .wim file can be used, depending on the purposes - patched BCD to %TFTPROOT%\Boot\BCD
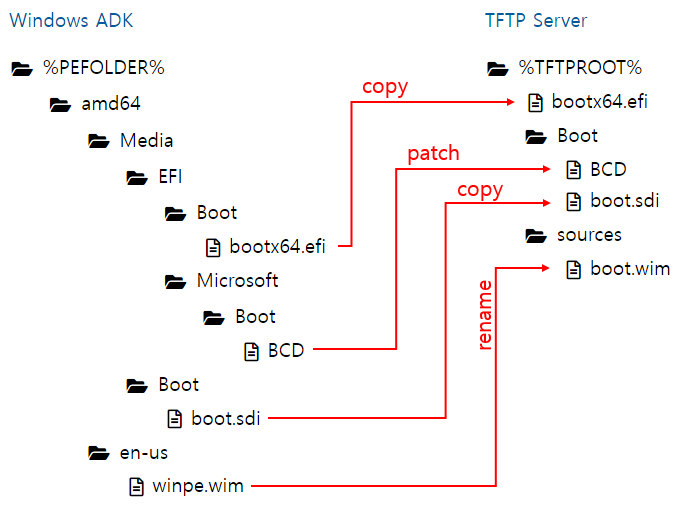
PXE would fail if TFTP directory and file structures are not properly set (e.g. capitalization mismatch on linux server)