I received my license today.

Hotspot on startup, armbian
Issue:
Use armbian-config to create a hotspot. The hotspot is well created, however, doesn’t start on next reboot. Have to go back to armbian-config and manage hotspot to start it again.
Solution:
/lib/systemd/systemd-sysv-install enable hostapd
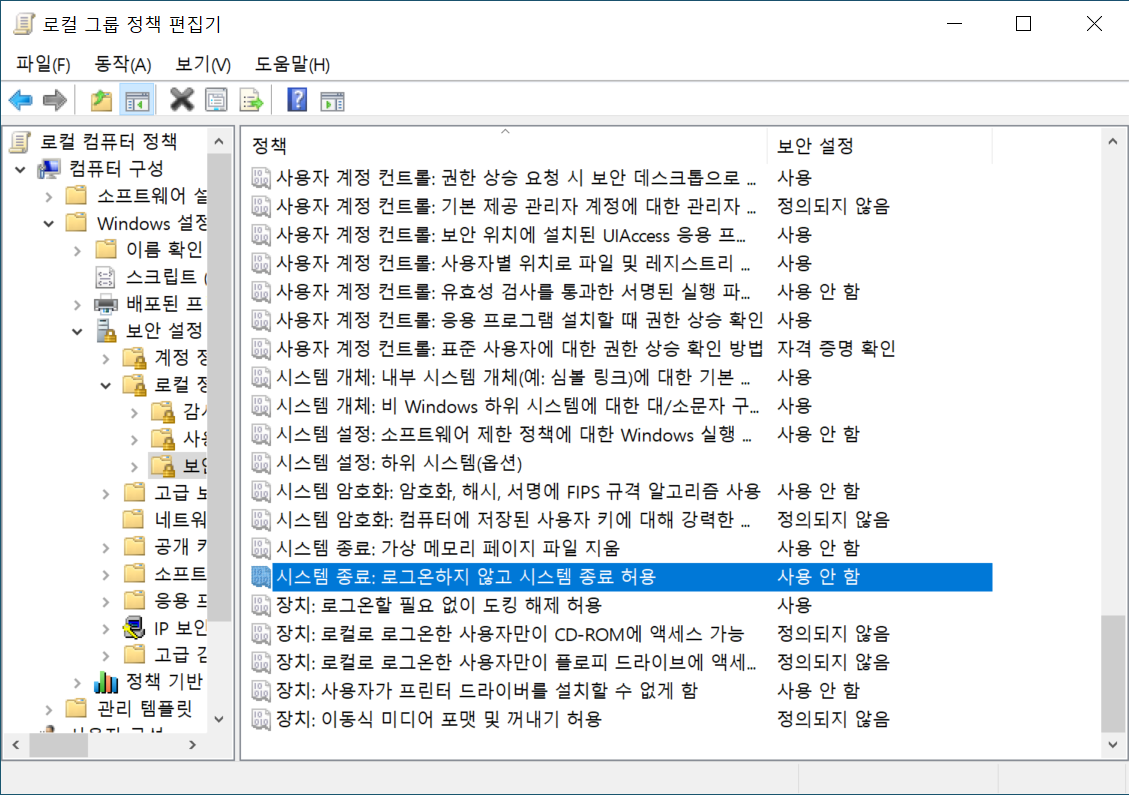
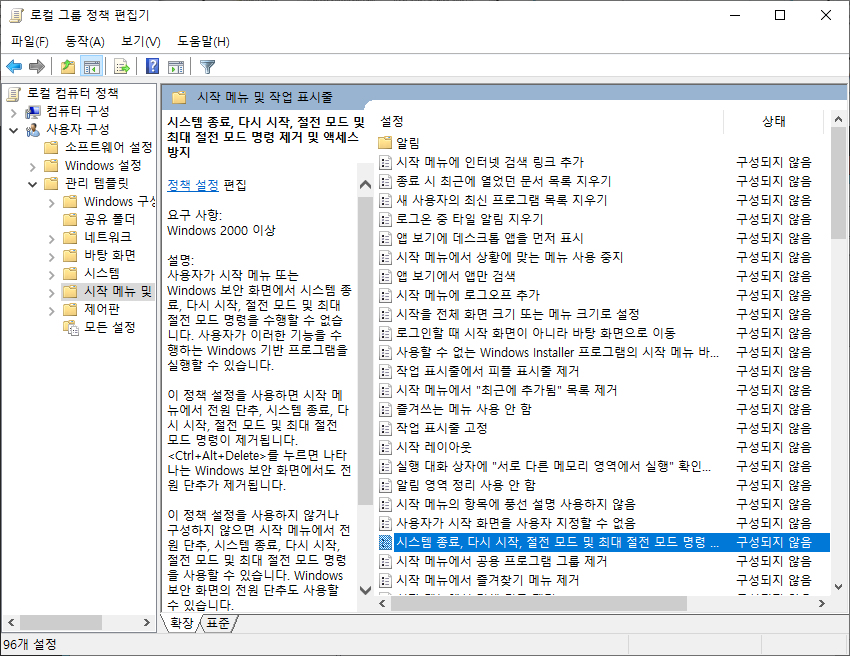
Windows 10 disable user shutdown
Systemctl enabling of OpenVPN
1. config file is in /etc/openvpn
sudo systemctl start/stop/status/enable/disable openvpn@[config]
2. config file is in /etc/openvpn/client
sudo systemctl start/stop/status/enable/disable openvpn-client@[config]
3. config file is in /etc/openvpn/server
sudo systemctl start/stop/status/enable/disable openvpn-server@[config]
extension of config should be .conf not .ovpn
Delete Team Project from the Team Foundation Server
C:\Program Files (x86)\Microsoft Visual Studio 11.0\VC>TfsDeleteProject /collection:https:[Team Foundation Service URL]/DefaultCollection [Team Project Name] 경고: 팀 프로젝트를 삭제한 후에는 복구할 수 없습니다. 모든 버전 제어, 작업 항목 추적 및 Team Foundation 빌드 데이터가 시스템에서 제거됩니다. 이 데이터를 복구하 려면 저장된 데이터베이스 백업을 복원해야 합니다. 팀 프로젝트 및 해당 데이터를 모 두 삭제하시겠습니까(Y/N)?y Build에서 삭제하는 중... 완료 버전 제어에서 삭제하는 중... 완료 작업 항목 추적에서 삭제하는 중... 완료 TestManagement에서 삭제하는 중... 완료 ProcessManagement에서 삭제하는 중... 완료 LabManagement에서 삭제하는 중... 완료 ProjectServer에서 삭제하는 중... 완료 경고. 보고서 서버 서비스를 찾을 수 없습니다. 경고. SharePoint 사이트 서비스를 찾을 수 없습니다. Team Foundation Core에서 삭제하는 중... 완료 C:\Program Files (x86)\Microsoft Visual Studio 11.0\VC>
Access Registry with PowerShell
Working with Registry is very similar to working with files and folders with PowerShell.
Set-Location cmdlet can set the current working location to registry.
PS C:\Windows\system32> Set-Location Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER PS Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER>
The registry provider’s full name is Microsoft.PowerShell.Core\Registry, but this can be shortened to just Registry.
PS C:\Windows\system32> Set-Location Registry::HKEY_CURRENT_USER PS Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER>
In addation, PowerShell has two pre-defined registry ‘drives’:
HKLM for HKEY_LOCAL_MACHINE
HKCU for HKEY_CURRENT_USER
PS C:\Windows\system32> Set-Location HKCU: PS HKCU:\>
However, other registry roots are not defined.
PS HKLM:\> Set-Location HKCR:
Set-Location : 드라이브를 찾을 수 없습니다. 이름이 'HKCR'인 드라이브가 없습니다.
위치 줄:1 문자:1
+ Set-Location HKCR:
+ ~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (HKCR:String) [Set-Location], DriveNotFoundException
+ FullyQualifiedErrorId : DriveNotFound,Microsoft.PowerShell.Commands.SetLocationCommand
PS HKLM:\>
You can define other roots by yourself with New-PSDrive cmdlet.
PS HKLM:\> New-PSDrive -Name HKCR -PSProvider Registry -Root HKEY_CLASSES_ROOT Name Used (GB) Free (GB) Provider Root CurrentLocation ---- --------- --------- -------- ---- --------------- HKCR Registry HKEY_CLASSES_ROOT PS HKLM:\> Set-Location HKCR: PS HKCR:\>
Modify File Time Stamps using PowerShell
Usages: (Get-Item [filename]).CreationTime = [date/time] (Get-Item [filename]).LastAccessTime = [date/time] (Get-Item [filename]).LastWriteTime = [date/time] PS C:\> (Get-Item .\test.txt).LastAccessTime = Get-Date → This command converts 'last access time' of 'test.txt' to current date and time PS C:\> (Get-Item .\christmas.tree).LastWriteTime = '2016-12-25 AM0:00' → This command converts 'last write time' of 'christmas.tree' to specific date and time
Batch Processing with ForEach:
Get-ChildItem | ForEach-Object { $_.LastWriteTime = Get-Date }
PS C:\> Get-ChildItem | ForEach-Object { $_.LastWriteTime = Get-Date }
→ This command converts 'last write time' to current date and time of all files in working directory
PS C:\> $i = 0; Get-ChildItem | ForEach-Object { $_.LastWriteTime = (Get-Date).AddDays(-1).AddMinutes($i++) }
→ This command converts 'last write time' to yesterday with increasing minutes
Check in/Check out files to/from the Team Foundation Server with command prompt
** Visual Studio 2017 Developer Command Prompt v15.0.26430.16
** Copyright (c) 2017 Microsoft Corporation
**********************************************************************
C:\>tf
Microsoft (R) TF – Team Foundation 버전 제어 도구, 버전 15.112.26421.0
Copyright (c) Microsoft Corporation. All rights reserved.
지원되는 버전 제어 명령 목록을 보려면 tf vc help를 입력합니다.
지원되는 Git 명령 목록을 보려면 tf git help를 입력합니다.
지원되는 서버 설정 명령 목록을 보려면 tf settings help를 입력합니다.
C:\>tf checkin
체크 인한 파일이 없습니다.
C:\>tf get
모든 파일이 최신 상태입니다.
C:\>
How to get the Executable name of a specific Window
RunAs.exe with /netonly and /savecred simultaneously
RunAs allows a user to run specific tools and programs with different permissions than the user’s current logon provides.
However, the paremeter /netonly and /savecred cannot be used same time.
We can use windows API ‘CreateProcessWithLogonW’ instead.
#pragma comment(lib, "Advapi32")
#include <windows.h>
BOOL RunAsNetOnly(LPCWSTR szUser, LPCWSTR szDomain, LPCWSTR szPass, LPCWSTR szApp)
{
// VARIABLE
STARTUPINFOW si;
PROCESS_INFORMATION pi;
// INIT
ZeroMemory(&si, sizeof(si));
ZeroMemory(&pi, sizeof(pi));
si.cb = sizeof(si);
return CreateProcessWithLogonW(szUser, szDomain, szPass, LOGON_NETCREDENTIALS_ONLY,
szApp, NULL, CREATE_DEFAULT_ERROR_MODE, NULL, NULL, &si, &pi);
}